In the fifth series of container networking we will see some more concepts of
how networking works in containers.
Pod to Pod Communication between multiple Nodes
In order to test this, we need to have a docker swarm started and run some services so that each container or service runs on different hosts. Lets check the available docker networks,
[root@manja17-I14021 ~]# docker network ls
Now start the docker swarm by advertising the current machine Host ip as
To add a worker to this swarm, run the following command:
docker swarm join \
Now if you see the available networks again ,we can see some more networks are created.
[root@manja17-I14021 ~]# docker network ls
We created a new network with overlay driver. Now lets run a container as a
Check the service ( i ran 2 replica of services )
If we see the service where it is running , we can see
 Lets inspect the network foobar as below,
Lets inspect the network foobar as below,
We can see a network space is available for the foobar and ip range is also available.Now if
Both the containers are created from the Overlay network foobar which has the IP

This is how multiple containers running on different hosts talk to each other. Now
lets move to kubernetes on how it does.
how networking works in containers.
Pod to Pod Communication between multiple Nodes
Before seeing how multiple pods talk to each other from different nodes, lets see
how we can let containers running on different nodes talk to each other in Docker.
Docker networking for multiple containers running on multiple hosts
how we can let containers running on different nodes talk to each other in Docker.
Docker networking for multiple containers running on multiple hosts
Communication between containers running on different hosts is done by using a
Overlay network in Docker. A Overlay network created a distributed network
among multiple docker daemon hosts. This network sits on the top ( over lay )
of the host specific network allowing containers connected to it to communicate securely. Docker will take care of handling the routing of packets from one docker daemon (host) to other docker daemon.
among multiple docker daemon hosts. This network sits on the top ( over lay )
of the host specific network allowing containers connected to it to communicate securely. Docker will take care of handling the routing of packets from one docker daemon (host) to other docker daemon.
In order to test this, we need to have a docker swarm started and run some services so that each container or service runs on different hosts. Lets check the available docker networks,
[root@manja17-I14021 ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
f5e39d24b3b2 bridge bridge local
d12415e63762 docker_gwbridge bridge local
45bcb2a8831c host host local
f3shhlxp5nkk ingress overlay swarm
9b57fcb59a81 none null local
Now start the docker swarm by advertising the current machine Host ip as
[root@manja17-I14021 ~]# docker swarm init --advertise-addr 10.131.36.181
Swarm initialized: current node (9mmp0gjkrt3v2nzznd4xqwlx3) is now a manager.
To add a worker to this swarm, run the following command:
docker swarm join \
--token SWMTKN-1-33zmzxrovk2hrqxkvyx2q1sncvr4zxpjo3yz56spr5xhi1czqf 786x60a6af138gn1mxypw85uk \
10.131.36.181:2377
From the other machine join to the swarm by running,
From the other machine join to the swarm by running,
[root@manja17-I14022 ~]# docker swarm join \
> --token SWMTKN-1-33zmzxrovk2hrqxkvyx2q1sncvr4zxpjo3yz56spr5xhi1czqf-786x60a6af138gn1mxypw85uk \
> 10.131.36.181:2377
This node joined a swarm as a worker.
Now we have 2 nodes in the swarm as below,
Now we have 2 nodes in the swarm as below,
[root@manja17-I14021 ~]# docker node ls
ID HOSTNAME STATUS AVAILABILITY MANAGER
9mmp0gjkrt3v2nzznd4xqwlx3 * manja17-I14021 Ready Active Leader
de5bmv3i3ygmpjbjbh2zskxk9 manja17-I14022 Ready Active
Now if you see the available networks again ,we can see some more networks are created.
Now lets create our own overlay network as
[root@manja17-I14021 ~]# docker network create -d overlay foobar
ae61hmk9cam26umcmg03tpcrr
[root@manja17-I14021 ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
ae61hmk9cam2 foobar overlay swarm
We created a new network with overlay driver. Now lets run a container as a
service using,
[root@manja17-I14021 ~]# docker service create --name testing-service --network foobar --replicas 2 alpine sleep 1d
3l7b1yfgxkjg979vr2m7mtx1b
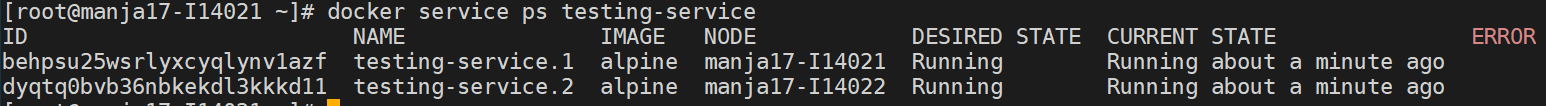
Check the service ( i ran 2 replica of services )
[root@manja17-I14021 ~]# docker service ls
ID NAME REPLICAS IMAGE COMMAND
3l7b1yfgxkjg testing-service 2/2 alpine sleep 1d
If we see the service where it is running , we can see
[root@manja17-I14021 ~]# docker network inspect foobar
[
{
"Name": "foobar",
"Id": "7f86pls6d118d3rfbx1ue8d7i",
"Scope": "swarm",
"Driver": "overlay",
"EnableIPv6": false,
"IPAM": {
"Driver": "default",
"Options": null,
"Config": [
{
"Subnet": "10.0.0.0/24",
"Gateway": "10.0.0.1"
}
]
},
"Internal": false,
"Containers": {
"283107f7c9ab3858488bc10aceb83d558aeb2755dae95718b398e836e101c871": {
"Name": "testing-service.1.behpsu25wsrlyxcyqlynv1azf",
"EndpointID": "aff02bb1394cd9ad850739fd91b8970587abebef9ff96b6897b28360632bd916",
"MacAddress": "02:42:0a:00:00:03",
"IPv4Address": "10.0.0.3/24",
"IPv6Address": ""
}
},
"Options": {
"com.docker.network.driver.overlay.vxlanid_list": "257"
},
"Labels": {}
}
]
We can see a network space is available for the foobar and ip range is also available.Now if
we see the containers starts for the testing-service we can get 2 containers running and
if inspect the container for their IP address we can see,
[root@manja17-I14021 ~]# docker inspect 283107f7c9ab | grep IPAddress | tail -n 1 "IPAddress": "10.0.0.3",
[root@manja17-I14022 ~]# docker inspect 0f0823bc2930 | grep IPAddress | tail -n 1
"IPAddress": "10.0.0.4",
Both the containers are created from the Overlay network foobar which has the IP
address range “10.00.0/24”. So now if we login to a container and try to ping other container we can see,
[root@manja17-I14021 ~]# docker exec -it 283107f7c9ab sh
/ # ping 10.0.0.4
PING 10.0.0.4 (10.0.0.4): 56 data bytes
64 bytes from 10.0.0.4: seq=0 ttl=64 time=0.798 ms
64 bytes from 10.0.0.4: seq=1 ttl=64 time=0.490 ms
^C
--- 10.0.0.4 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 0.490/0.644/0.798 ms
/ # exit
The Over lay network will be created bridging the two hosts as below,
The Over lay network will be created bridging the two hosts as below,
This is how multiple containers running on different hosts talk to each other. Now
lets move to kubernetes on how it does.


No comments :
Post a Comment